It often happens while pentesting to encounter restrictions on various parameters on Windows systems. Constrained environments such as remote desktops, “kiosks” etc. are usual starting points for security professionals. Hence, bypassing restrictions on these machines is a skill that proves useful during penetration tests.
One of the first mechanisms on Windows explorer we will see exists to prevent users from accessing the filesystem of the different plugged-in disks. Mostly the purpose of it is to hide drives (especially the system drive) from regular, non-administrator, users, giving a feeling of protection to organisations deploying such mechanisms.
We will see in what consist these protections, how it is configured and how to bypass it.
Unconstrained environment
In an unrestricted environment, users can access the different drives of the machine using file explorer, explorer.exe:
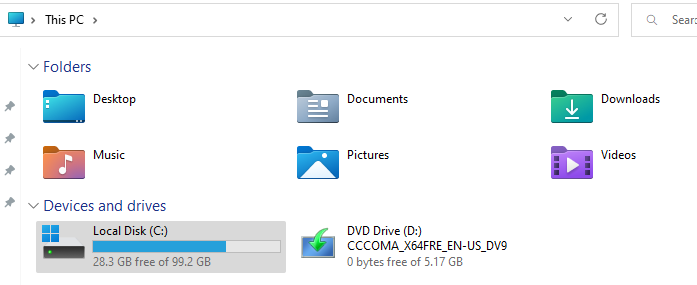
Double-clicking on the drive icon will then give access to file and folders stored on it:
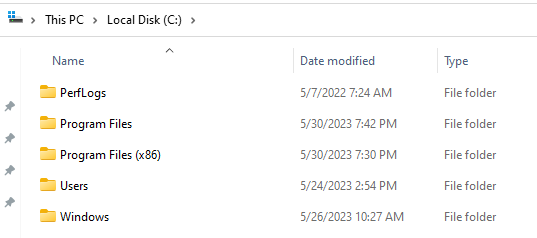
It is also possible for them to type it in the upper bar of explorer to access it:
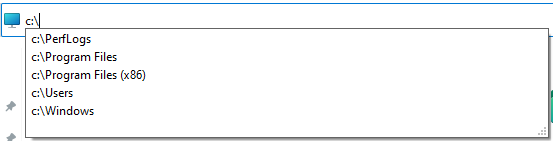
Note that Windows tries to autocomplete paths automatically.
There are many other ways for a user to access the drive, using the explorer “save as” feature, by printing a document, with browsers etc.
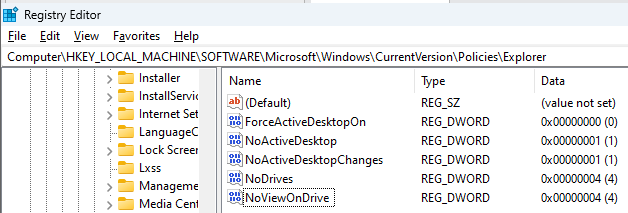
NoDrives
According to Microsoft,NoDrives :
Removes the icons representing selected drives from My Computer and from Windows Explorer. Also, the drive letters representing the selected drives do not appear in the standard Open dialog box. This entry stores the setting of the Hide these specified drives in My Computer Group Policy.
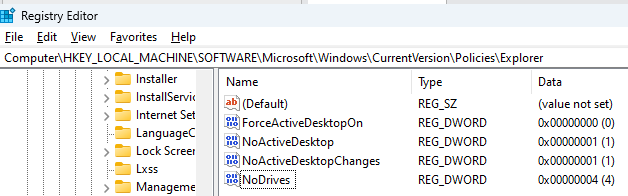
The NoDrives parameter is controlled via local policies and is technically declined via a registry key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoDrives
The key can take several values which is a sort of bitmask of what drive can be seen from a user perspective:
| Value | Meaning |
|---|---|
| 0x0 | Do not restrict drives. All drives appear. |
| 0x3 | Restrict A and B drives only. |
| 0x4 | Restrict C drive only. |
| 0x7 | Restrict A, B, and C drives only. |
| 0x8 | Restrict D drive only. |
| 0xF | Restrict A, B, C, and D drives only. |
| 0x03FFFFFF | Restrict all drives. |
SS64.com has a nice calculator for mapping values to drives.
If we create the corresponding key on a machine with the value 0x4 for the C: drive for example:
We can see that the C: drive disappear from explorer for the user:
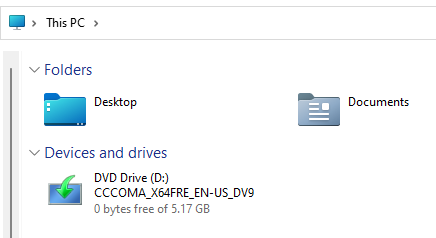
Bypasses
As NoDrives is mostly a visual restriction, accessing the drives using explicit path still works. In our C: example, you can just type in the upper bar C: and then ENTER:

Autocompletion also still works with NoDrives so you can partially list the drive using the explorer upper bar for example:
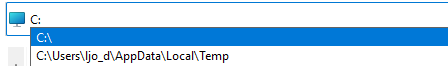
If you have no access to the file explorer, the Windows Run box can be used:
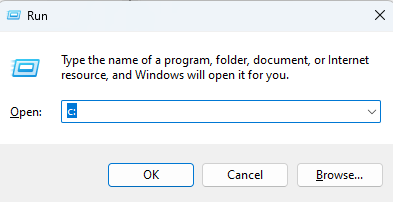
Or Microsoft Edge:
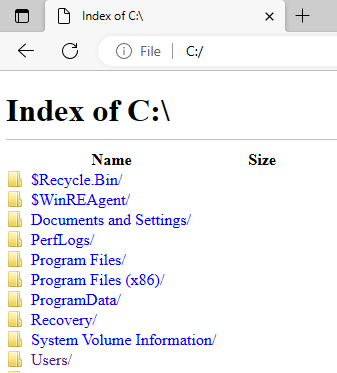
NoViewOnDrive
In conjunction with NoDrives, the NoViewOnDrive restriction can be enabled. According to Microsoft it:
Prevents users from using My Computer to access the content of selected drives.
When a drive is represented in the value of this entry, users cannot view the contents of the selected drives in My Computer or in Windows Explorer. Also, they cannot use the Run dialog box, the Map Network Drive dialog box, or the Dir command to view the directories on these drives.
It is also controlled via local policies and has an associated registry key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoViewOnDrive
Values of the above key follow the same table than NoDrives.
We set it to the value 0x4 corresponding to the C: drive on our test sytem:
Users are now restricted in what they can see from explorer by typing C: in the upper bar for example:
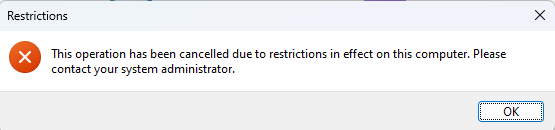
Trying to access it via Run will provoke the same message than above to be displayed.
Bypasses
Using Edge still allows users to view the forbidden drive:

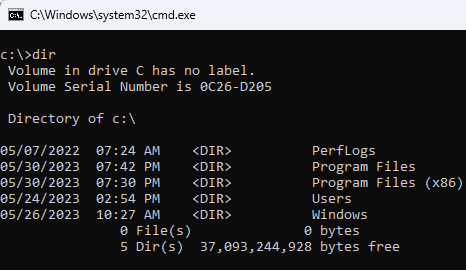
If you have access to a CLI such as cmd.exe or powershell.exe, it is also a bypass:
You can also map a network drive to the local C::
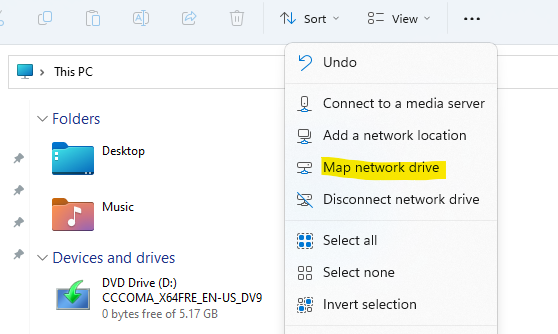
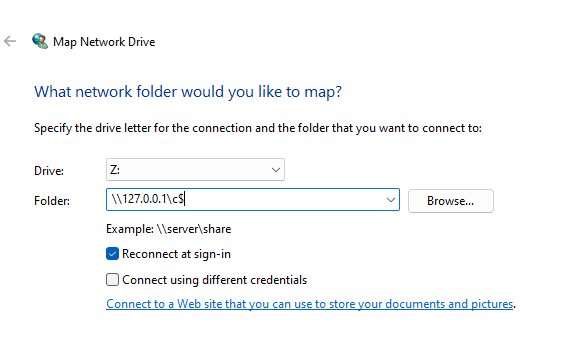
And access it afterwards using explorer:
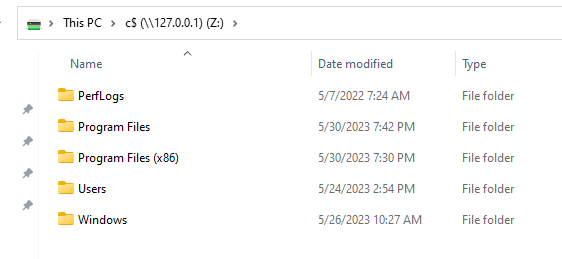
Basically, any program other than explorer.exe or other native Windows GUI programs will bypass the restriction.
NoNetConnectDisconnect
To restrict the above network map bypass on NoViewOnDrive, another parameter named NoNetConnectDisconnect exists. According to Microsoft it:
Prevents users from using Windows Explorer or My Network Places to either map or disconnect network drives.
It is also controlled via the local policies and has an associated registry key:
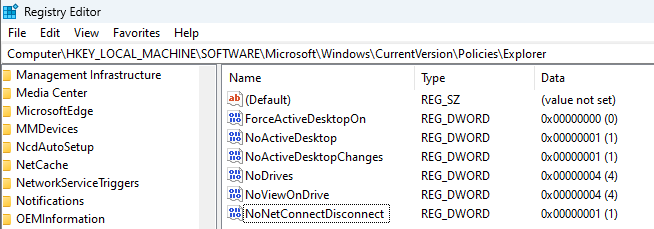
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoNetConnectDisconnect
Value can be set to 0 for no restriction or 1 to enable it. Once it is enabled, unprivileged users can no longer map network drives via explorer, which may be an issue depending on one organisation’s needs.
We set it on our environment:
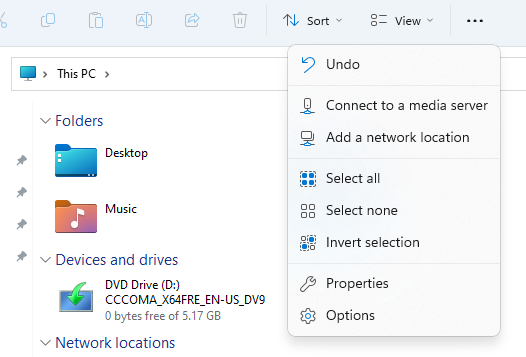
Users can no longer map network drives from explorer:
Bypasses
Access the local C: drive from the loopback without creating a mapping:
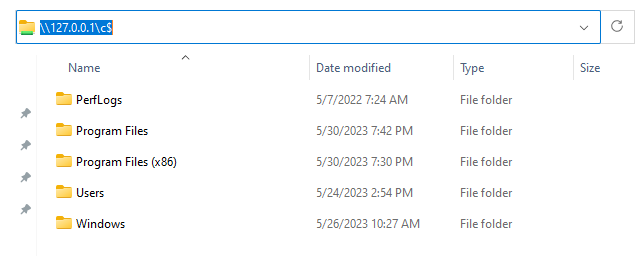
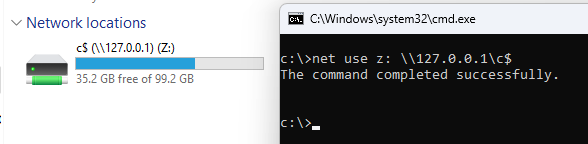
Create a mapping from the CLI as NoNetConnectDisconnect is a visual restriction with net use <drive> <net_path>:
Or use Microsoft Edge.
Conclusion
Knowing how to bypass Windows explorer restrictions is useful, especially when this type of restriction is the first step to be able to do anything else as an attacker.
Through the above example of filesystem, you saw that Microsoft’s restrictions are far away from being bulletproof and that many ways exists to bypass it.
Many other parameters are used by Microsoft to restrict explorer and other GUI components. I plan to post on other restrictions soon, so stay tuned.
In the meantime, you can read a good article on command-line restrictions evasions by Martin Sohn Christensen: The command prompt has been disabled by your administrator. Press any key to continue… or use these weird tricks to bypass – admins will hate you! — Improsec | improving security.
