TL;DR; Malwarebytes' software for firewall management let unprivileged users perform administrative firewall actions without access controls allowing for local network rules bypass.
Timeline
- 24-05-2023: Vulnerability reported on Malwarebytes' HackerOne program
- 06-06-2023: Malwarebytes' close the report as informative with “no security impact”
- 06-06-2023: Report was reopened after more information was given
- 06-06-2023: Report was closed again as informative with “it appears this is intended behavior as the application can be locked using a password.”
- 21-06-2023: Report was locked by Malwarebytes / Current article published
- 25-06-2023: CVE-2023-36631 assigned
Windows Firewall
The Windows Defender Firewall with Advanced Security is defined as such by Microsoft:
Windows Defender Firewall with Advanced Security is a host firewall that helps secure the device in two ways. First, it can filter the network traffic permitted to enter the device from the network, and also control what network traffic the device is allowed to send to the network.
Seeing and defining firewall rules are possible by using that default Microsoft tool:
This is the MMC snap-in:
The Windows Defender Firewall with Advanced Security MMC snap-in is more flexible and provides much more functionality than the consumer-friendly Windows Defender Firewall interface found in the Control Panel. Both interfaces interact with the same underlying services, but provide different levels of control over those services.
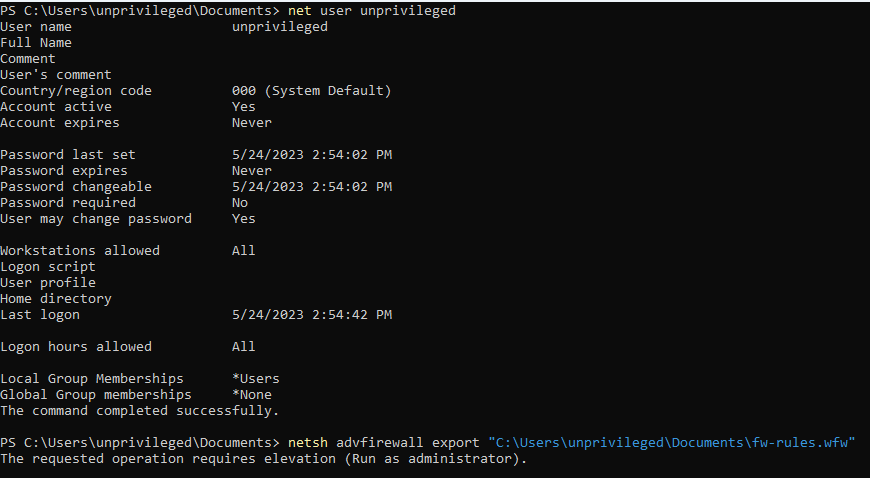
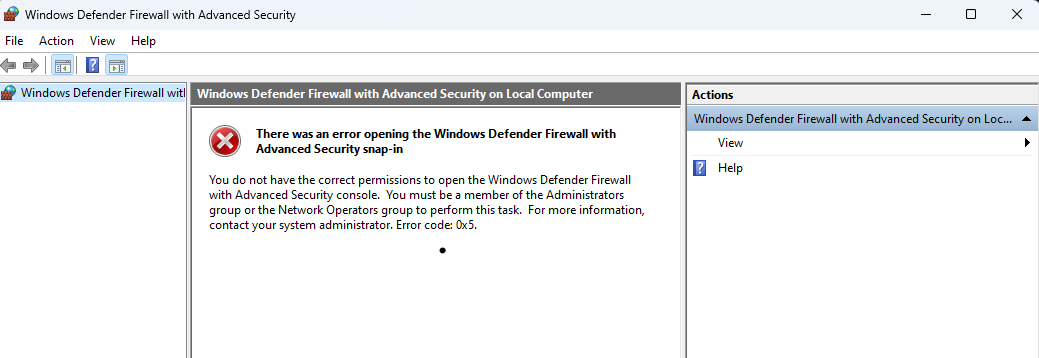
However the actions possible with that tool are restricted to either the local administrator or the network administrator group. Trying such actions with an unprivileged user will result in a permission denied error:
Same from the GUI:
Malwarebytes' Windows Firewall Control
Windows Firewall Control is a product from Binisoft (one of Malwarebytes companies). Description of the product from the vendor website is as such:
Windows Firewall Control is a powerful tool which extends the functionality of Windows Firewall and provides new extra features which makes Windows Firewall better. It runs in the system tray and allows the user to control the native firewall easily without having to waste time by navigating to the specific part of the firewall.
It can be installed pretty quickly by an administrator:
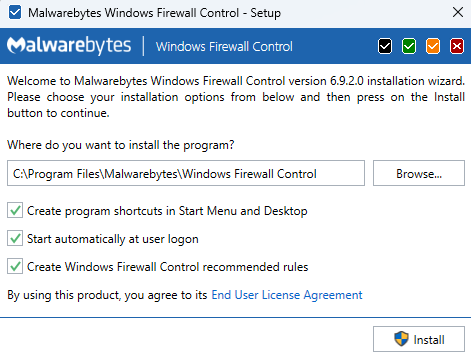
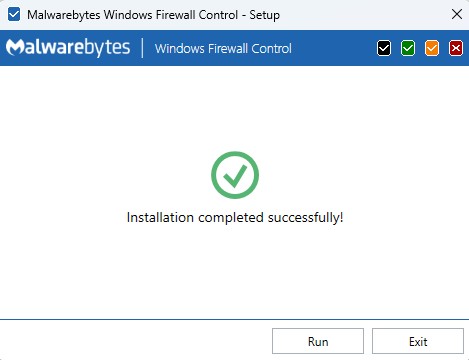
(Note for later that no lock password was asked)
Once installed, it appears in the system tray of any user that launch the wfc.exe binary from the installation folder (that is, any local user):

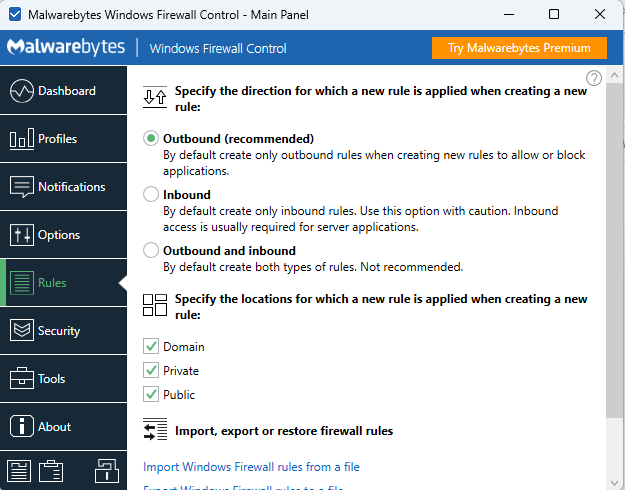
And the graphical interface can be started to execute different actions related to firewall administration:
Two executables are running under the hood, a privileged service wfcs.exe and the GUI tool wfc.exe:

Basically, the GUI is giving order to the service for privileged actions.
The issue
The wfc.exe binary allow unprivileged users to execute Windows Defender Firewall with Advanced Security actions by using the Main Panel > Rules tab without applying additional access controls.
Amongst the possible actions there are:
- Exporting firewall rules; which leaks current rules to an attacker.
- Importing firewall rules; which can allow an attacker to completely bypass the firewall rules by overwriting existing rules.
- Resetting firewall rules to default; which could also allow an attacker to bypass custom rules that were added after the defaults ones.
This issue basically give full firewall control to unprivileged users.
PoC
Export feature:
- Open the Malwarebytes Windows Firewall Control via the system tray and clicking
Main Panelor by double-clickingwfc.exein the installation folder - Go to
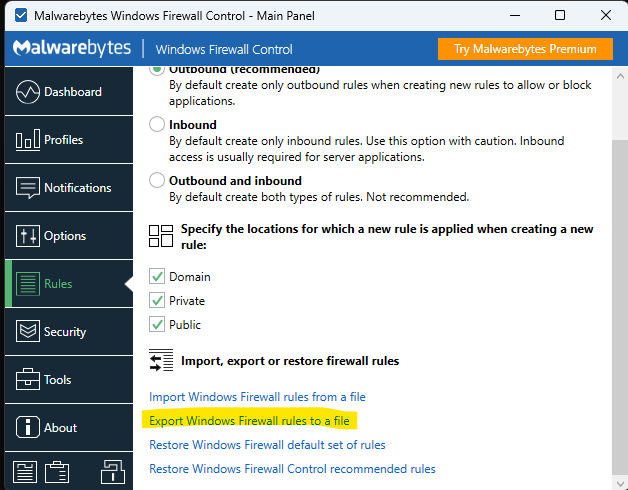
Rulestab - Click the
Export Firewall rules to a filelink:
- Save the file to a location with write permissions for the user:
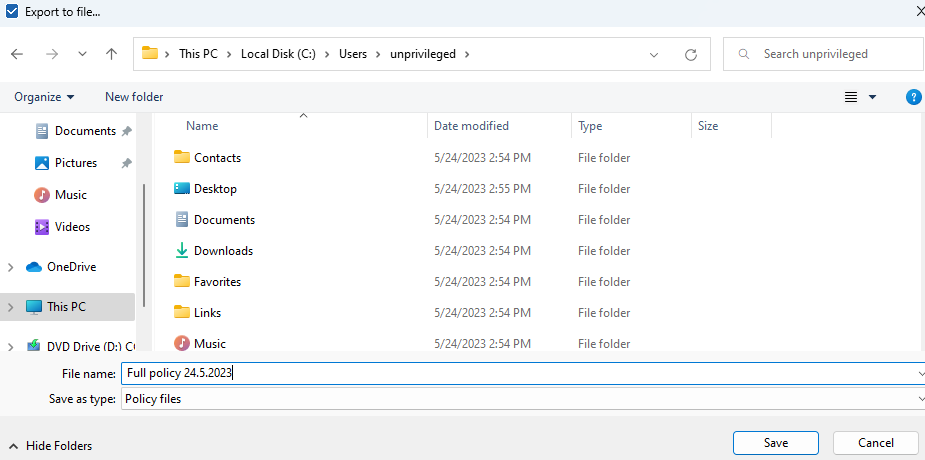
The exported file is successfully saved and readable:
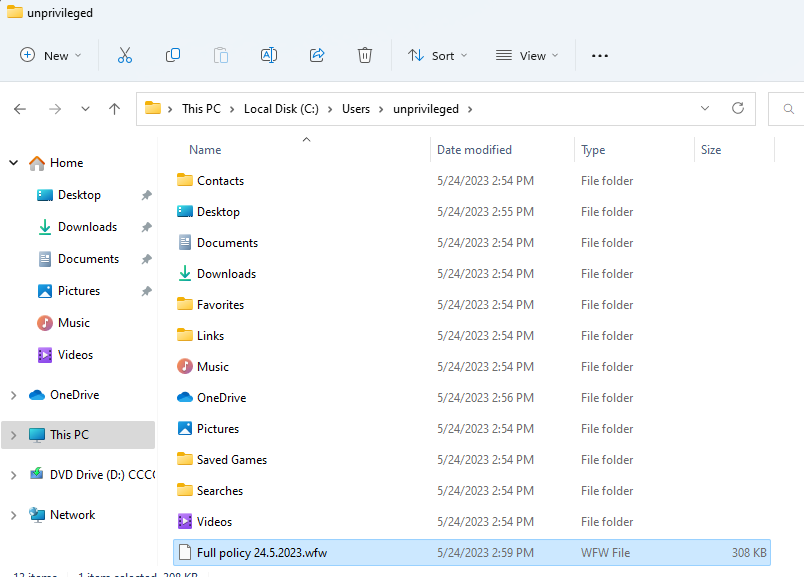
Restore feature:
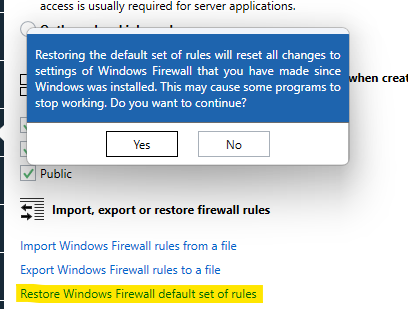
Note that it is also possible to use the Restore Windows Firewall default set of rules feature in the same fashion:
Import feature:
The “Import Windows Firewall rules from a file” is also working, which can allow an attacker to erase current rules, whitelist any network flow, and totally bypass the firewall:

Conclusion
Malwarebytes was reached through its HackerOne’s bug bounty program, the report was closed as informative and their answer was the following:
After discussing this internally, it appears this is intended behavior as the application can be locked using a password.
No lock password is asked on default installation which means users are vulnerable by default unless an administrator did set up a password after installation.
The same lack of access control was reported in 2022 on another tab of the software, this time allowing local privilege escalation: CVE-2022-25150 : In Malwarebytes Binisoft Windows Firewall Control before 6.8.1.0, programs executed from the Tools tab can be used to es (cvedetails.com)
References
- Windows Defender Firewall with Advanced Security - Windows Security | Microsoft Learn
- https://hackerone.com/reports/2000375 (I doubt this will ever be disclosed but who knows)
